TISAX® stands for Trusted Information Security Assessment Exchange and is a registered trademark of the ENX Association. TISAX® is an assessment and exchange procedure for information security in the automotive industry.
It was developed by the German Association of the Automotive Industry and is now managed by the ENX Association. It provides a standardized approach to auditing and certifying the information security of companies operating in the automotive industry.
TISAX® is based on the international standard ISO/IEC 27001 and includes specific requirements of automotive manufacturers. We have compiled this article for you based on the experience of 50 projects.
The costs of implementing and certifying according to ISO 27001 vary depending on the company’s size and complexity, as well as other factors, which we will cover below.
What is TISAX® and why is certification important?
This certification is crucial for companies in the automotive industry, as information security in this sector is particularly sensitive. By meeting the requirements of TISAX®, suppliers and service providers can prove that they meet the necessary standards for protecting information. Depending on the requirements, certification takes place at different assessment levels (Level 2 and Level 3). Companies that obtain TISAX® certification help to strengthen information security throughout the supply chain.
The ENX Association is an independent organization that accredits assessment providers. It does not offer advice or support in preparation for the TISAX® assessment. Obtaining TISAX® certification requires considerable resources and financial means. The assessment objectives must be clearly defined and achieved to meet the requirements for TISAX®.
Basics and significance of TISAX®
The certification is divided into 3 levels, with Level 1 having the lowest requirements and Level 3 the highest. Companies in the automotive industry and their suppliers must fulfill the requirements for TISAX® certification in order to prove their information security. This is particularly important in the automotive industry, where the protection of sensitive data and prototypes is critical.
To obtain TISAX® certification, companies must meet the TISAX® requirements, which help to build trust with customers and partners. Assessment service providers offer advice and support in preparing for the TISAX® assessment to ensure that companies achieve the objectives set.
The requirements for TISAX® levels 1 to 3 can be described as follows:
TISAX® Level 1:
Companies can carry out the TISAX® Assessment Level 1 themselves via a self-assessment. For TISAX Level 1, an assessment of the company based on the ISA questionnaire is required, but this is not reviewed. Since the measures are not checked objectively and the company alone is responsible for the results, this has little significance in practice.
TISAX® Level 2:
The security requirements of a company are classified as high at Level 2. In a Level 2 assessment, the company’s self-assessment is confirmed by a TISAX assessment company approved by ENX. The audit is carried out based on the company’s documentation.
TISAX® Level 3:
Level 3 according to TISAX® means that the need for protection is classified as “very high”. It is the highest security level for companies in the automotive industry. At Level 3, on-site inspections and live interviews are carried out by an auditor. Documents and evidence are checked, local conditions are considered, process implementation is observed and unplanned interviews are conducted with process participants. An accredited auditor conducts an on-site assessment of the maturity level of the Information Security Management System (ISMS) at each of the company’s locations.
These descriptions provide an overview of the respective expectations and the level of security that organizations must achieve at the various TISAX® levels.
Advantages of TISAX® certification
By meeting the requirements for information security in the automotive industry, car manufacturers can ensure that their ISMS is managed and monitored.
The VDA-ISA questionnaire serves as a central platform for defining the requirements and monitoring the entire process. Suppliers and service providers can ensure that they achieve all assessment objectives and implement continuous improvement in their system by preparing for the TISAX® assessment. In this way, TISAX® certification helps to standardize and document the process.
What are the differences between TISAX® and ISO 27001?
The differences between TISAX® and ISO 27001 lie mainly in the specific objectives that must be met. While ISO 27001 defines general requirements for information security management systems, the TISAX® requirements are tailored specifically to the automotive industry.
While there is no standardized process for ISO 27001 certification, there are proofs of the requirements for TISAX® that must be fulfilled. Companies must fulfill several requirements to obtain TISAX® certification, while ISO 27001 specifies an established process that must be followed.
What do TISAX® and ISO27001 have in common?
The ISO 27001 and TISAX® certifications have significant similarities. This makes it possible to work on both certification projects in parallel and manage them together, although this certainly means additional work.
We have written a detailed post on the differences and similarities between ISO 27001 and TISAX®.
TISAX® certification already covers up to 70% of the requirements of the new NIS2 directive.
What requirements must be met for TISAX® certification?
The TISAX® requirements are defined in the requirements catalog of the German Association of the Automotive Industry. An assessment according to TISAX® must be carried out in which the legal requirements and the associated requirements are checked. The ISA questionnaire serves as a testing and exchange mechanism.
The maturity model distinguishes between 6 maturity levels:
Maturity level
Terminology
Description
0
Incomplete
There are no documented security measures or guidelines. Information security is not considered or neglected.
1
Performed
There are some documented security measures, but clear policies and processes are lacking. Information security is poorly managed and inconsistent.
2
Managed
There are documented security guidelines and processes, but their implementation is incomplete or inadequate. Information security is considered sporadically.
3
Established
Security measures are largely documented and implemented, but regular reviews and improvements are lacking. Information security is consistent.
4
Predictable
Security measures are documented, implemented, and regularly reviewed. There is a formal process for security assessment and improvement. Information security is proactively managed.
5
Optimizing
The security measures are documented, implemented, and continuously improved. There is a formal process for the ongoing monitoring, measurement, and optimization of information security.
Requirements for information security according to TISAX®
Companies must meet certain expectations about structure and information security to receive TISAX® certification. These include the defined objectives, which follow a standardized process.
Companies must fulfill the requirements of the VDA’s ISA questionnaire if they intend to obtain TISAX® certification.
The certification confirms that the company has taken the necessary measures to ensure information security. It also confirms that the company explicitly follows the requirements according to the TISAX® questionnaire. This enables the company to gain a competitive advantage and build trust with customers and partners.
An overview of the VDA ISA questionnaire and its significance for the automotive industry.
The requirements for information security are defined in the ISA questionnaire. The ISA questionnaire is a tool used by the automotive industry to assess and improve information security within companies.
It provides a structured approach to identifying security risks and implementing appropriate measures to protect sensitive information. The importance of this catalog for the automotive industry lies in its ability to help companies meet the increasing requirements for data protection and information security.
Audit objectives and protection requirements in the TISAX® audit
There are eight TISAX® audit objectives, each of which defines specific requirements for TISAX®certification: Two for the security of information, four for the protection of prototypes and test vehicles, and a further two for data protection.
Objective
Handling information with different protection requirements
Appropriate security measures must be implemented to ensure that information is classified, processed and stored according to its protection needs. This can be achieved through encryption, access controls and information classification policies.
Protection of prototype components
Prototype components must be protected to prevent unauthorized access and theft. This can be achieved through physical security measures such as secure storage and access restrictions.
Dealing with prototype vehicles
Prototype vehicles must be protected from unauthorized access to ensure the confidentiality of development projects. Access controls and monitoring systems are crucial here.
Dealing with test vehicles
Test vehicles must be protected according to their sensitivity in order to minimize potential safety risks during the test phase. Access controls and monitoring systems are necessary.
Organization of events with prototype vehicles
At events where prototype vehicles are presented, security measures such as access controls and monitoring systems must be implemented to prevent theft or damage.
Data protection
Data protection regulations must be adhered to in order to protect personal data from unauthorized access, loss, or misuse. This includes measures such as data protection guidelines, access controls, and data protection training. The basis is the GDPR.
Personal data protection
Personal data must be protected according to the applicable data protection regulations. This includes compliance with data protection laws such as the GDPR and the implementation of appropriate technical and organizational measures to protect this data.
The TISAX® certification process is complex and requires regular renewal every three years through recertification.
How can the TISAX® requirements be successfully implemented?
Tips for documentation and verification
Careful documentation and verification are essential for the successful implementation of TISAX® requirements. The first step is to conduct a detailed analysis of all requirements to ensure that all relevant aspects are covered.
- Clear documentation of all the actions taken is crucial to complete the certification process successfully. Storing all relevant evidence in a well-organized system is recommended so that it can be presented quickly if required.
- In addition, regular reviews of the measures implemented should be carried out to ensure compliance with the specified targets in the long term. Companies that have followed an established process can hold their own against companies without certification.
- There is no predefined process to fulfill the requirements. However, you should have followed a documented process. The Information Security Assessment Catalog supports companies in meeting the TISAX® requirements, building a secure system, and maintaining it in daily operations.
Consultants can help to fulfill the requirements for certification according to TISAX® in the audit
- Consultants help companies prepare for TISAX® certification with a gap analysis to meet the stringent assessment objectives.
- They can help to develop and implement security measures and data protection standards to meet the TISAX® requirements.
- Consultants also offer training courses and workshops to inform employees about the requirements of TISAX® and to prepare them for the audit.
- They can help companies optimize internal processes to meet TISAX® requirements and assist in preparing the required documentation.
- While consultants prepare companies for the audit, they do not conduct formal audits or prepare official audit reports.
The role of audit service providers in the TISAX® certification process
- Audit providers are responsible for conducting the actual TISAX audits, also known as assessments.
- They must be officially approved and qualified by the ENX Association to carry out the task.
- Please note that the ENX Association assumes no responsibility for the specifications explicitly defined in a TISAX® manual.
- Their main task is to check the TISAX® requirements and assess whether a company meets the requirements.
- A standard process is followed to ensure that the overall system is integrated.
- Auditors conduct audits to ensure that the company has implemented the necessary security measures and meets data protection standards.
- On completion of the audit, auditors prepare a report containing their audit results and any recommendations for improvement.
Overall, auditors and consultants often work hand in hand, with consultants helping companies prepare for TISAX certification, while assessors carry out the formal audits and evaluate compliance.
What steps are necessary to obtain TISAX® certification?
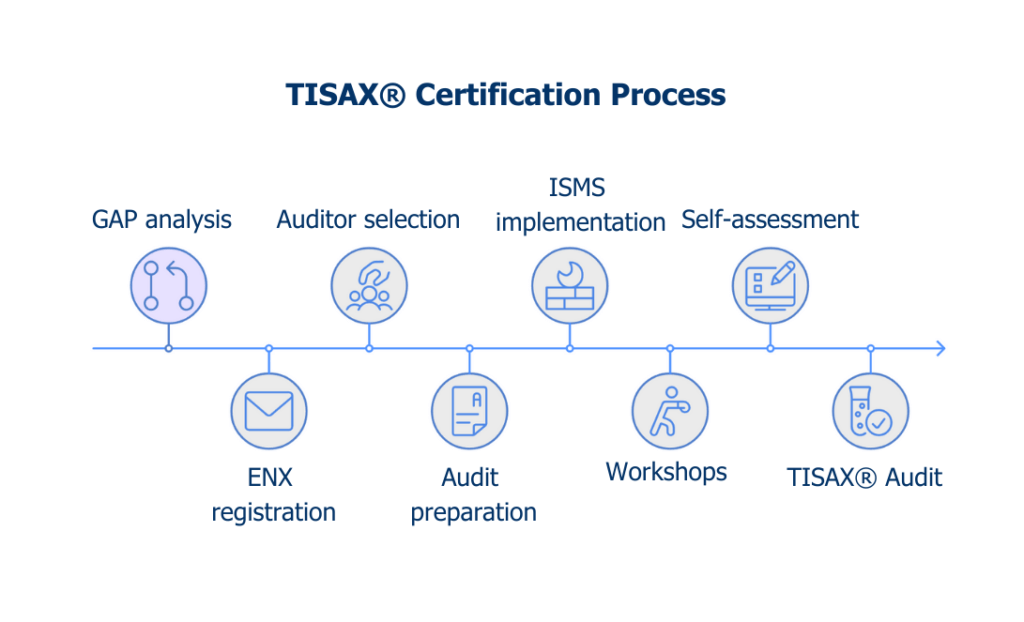
What is the process from gap analysis to successful TISAX® certification?
- GAP analysis: In this phase, a comprehensive analysis is carried out to identify the gaps between the current processes and the requirements of the TISAX® standards. This helps to develop a detailed action plan.
- ENX registration: Registration with ENX takes place after the GAP analysis. This is a necessary step to start the certification process. We will be happy to help you with the registration process.
- Auditor selection: This is where you select an ENX-approved auditor to perform the TISAX® assessment. The choice should be based on experience, expertise, and cost. With our extensive experience, we can assist you in the selection process.
- Audit preparation: In this phase, you prepare your company for the upcoming audit. This includes training staff, reviewing security policies and procedures, and ensuring all requirements are met.
- ISMS establishment and implementation: This involves implementing your company’s information security management system (ISMS) and establishing security policies, procedures, and controls.
- Workshops: We conduct workshops with you to increase awareness and understanding of the requirements of the TISAX® standards. They also serve to train staff in the relevant security practices.
- Self-assessment: Before the actual audit, you carry out a self-assessment. This allows you to assess your maturity level for the audit and close any gaps.
- TISAX® Audit: Finally, the TISAX® audit takes place. The selected assessor will evaluate compliance with the TISAX® standards. After a successful audit, you will receive the desired TISAX® label.
Clearly described, documented and verifiably practiced processes make it easier for everyone involved in the organization to understand and implement the steps to successful TISAX® certification. We would be happy to support you in this process.
The process from preparation to successful TISAX® certification begins with an understanding of the assessment objectives and requirements of the ISA requirements catalog. The requirements must be carefully implemented in order to create a solid foundation for certification.
Achieve a comprehensive understanding of TISAX® compliance so that all relevant aspects are covered. Supporting measures such as training and internal audits are also a must to establish and maintain TISAX® in daily business operations. Ultimately, consistently implementing these steps leads to successful certification and demonstrates a company’s commitment to sensitive data security and protection.
The expenditure and costs associated with TISAX® certification
The expenditure and cost of a TISAX® certification can vary depending on the company and its requirements. Estimating the potential costs and effort in advance and planning accordingly is important to ensure a smooth certification process.
The maturity level of your company is decisive for the costs. The project duration and the resulting costs range from 3-12 months and 25,000 – 50,000€. If you would like to learn more about the cost of TISAX®, please click here to read our Blog Post.
Can small companies meet the requirements of TISAX® certification?
Yes, small companies definitely can meet the requirements of TISAX®. The ISA questionnaire is designed in such a way that even small companies can work with it. The TISAX® requirements should be seen as guidelines that can be flexibly implemented to achieve adequately the desired audit objectives and the required protection.
Audit service providers determine the appropriateness for each company individually. However, both the establishment of an ISMS and the audit itself require a certain amount of effort and cost. For this reason, we advise micro-enterprises to consider whether the effort and potential benefits of TISAX® certification are economically justifiable.
Our practical tips for meeting the TISAX® requirements as more than 30 projects
The processes in which owners must be involved in a TISAX® project are listed below:
- Management: A TISAX® project is not possible without management support. The first requirement is therefore fulfilled if management support is available.
- HR: Efficient hiring, the definition of sensitive activities, and on-off boarding processes are the important parts of a TISAX® project. The planning and implementation of training courses are also part of the HR department’s responsibilities.
- Facility management: Physical security, security zone concept measures, emergency plans, and emergency drills are must-haves for successful TISAX® projects.
- IT: Self-explanatory. The IT is responsible for 60% of a TISAX project. Regardless, the interfaces between IT and other departments must be defined and documented.
- Purchasing: Information security relevant suppliers and non-disclosure agreements are critical parts of a TISAX® project.
- Compliance: The data protection officer (DPO) – if available – and, depending on the company size, the legal department should participate.
- Time: A TISAX® project and the maturity of an ISMS take time. A successful TISAX® project should be expected to take at least 6 months. For larger companies and depending on the maturity of the existing processes, this period can be up to 12 months.
About the Author

Can Adiguzel is the founder of 360 Digital Transformation. He is a TISAX consultant and ISO 27001 Lead Auditor. He has been working in IT project management for more than 11 years. His passion is information security for SMEs and he helps SMEs overcome their information security challenges with a hands-on consulting approach.

